Abstract
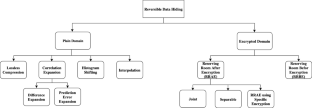
The goal of this survey is to review the state-of-the art Reversible Data Hiding (RDH) methods, classify these methods into different classes, and list out new trends in this field. RDH, in general, is a challenging problem and has potential applications in the today’s digital world. Reversible data hiding methods not only securely transfer secret data but also recover the cover media faithfully. Recently, RDH methods are mainly focused on obtaining high capacity along with tuneable quality. Although, extensive investigations in the field of reversible data hiding was carried out in the recent past, a comprehensive review of existing literature for listing out research gap and future directions has not yet been reported. In this survey, we have classified the reversible data hiding methods mainly into a) Plain domain b) Encrypted domain and also examine their pro and cons. Tabular comparison of various RDH methods has been provided considering various design and analysis aspects. Moreover, we discuss important issues related to reversible data hiding and use of benchmarked datasets along with performance metrics for evaluation of RDH methods.




Similar content being viewed by others
References
Barton JM (1997) Method and apparatus for embedding authentication information within digital data. U.S. Patent, 5,646,997
Honsinger CW, Jones P, Rabbani M, Stffel JC (2001) Lossless recovery of an original image containing embedded data. U.S. Patent,6,278,79
Fridrich J, Goljan M, Du R (2001) Invertible authentication. Proc SPIE Security and Watermarking of Multimedia Contents 4314:197–208
Goljan M, Fridrich JJ, Du R (2001) Invertible authentication. Proceedings 4th Inf Hiding Workshop 4314:197–208
Fridrich J, Goljan M, Du R (2002) Lossless data Embedding-New paradigm in digital watermarking. EURASIP J Adv Signal Process 2:185–196
Xuan G, Zhu J, Chen J, Shi YQ, Ni Z, Su W (2002) Distortionless data hiding based on integer wavelet transform. IEEE J Electron lett 38:1646–1648
Kalker T, Willems FMJ (2002) Capacity bounds and constructions for reversible data-hiding. In: 14th International Conference on Digital Signal Processing Proceedings. DSP 2002 (Cat No.02TH8628), vol 1, pp 71–76
Celik MU, Sharma G, Tekalp AM, Saber E (2002) Reversible data hiding. Proceedings. International Conference on Image Processing 2:157–160
Celik MU, Sharma G, Tekalp AM, Saber E (2005) Lossless generalized-LSB data embedding. IEEE Transactions on Image Processing 14:253–266. https://doi.org/10.1109/TIP.2004.840686
Chen LST, Lin SJ, Lin JC (2010) Reversible JPEG-based hiding method with high high hiding-ratio. Int J Pattern Recognit Artif Intell 24:433–456. https://doi.org/10.1142/S0218001410007968
He J, Pan X, Wu HT, Tang S (2020) Improving block ordering and frequency selection for reversible data hiding in JPEG images. Signal Process 107647:175. https://doi.org/10.1016/j.sigpro.2020.107647
Zhang W, Chen B, Yu N (2011) Capacity-approaching codes for reversible data hiding. Lecture Notes in Computer Science, Springer 6958:255–269. https://doi.org/10.1007/978-3-642-24178-9_18
Lin S, Chung W (2012) The scalar scheme for reversible Information-Embedding in Gray-Scale signals: capacity evaluation and code constructions. IEEE Transactions on Information Forensics and Security 7(4):1155–1167. https://doi.org/10.1109/TIFS.2012.2197614
Bao F, Deng RH, Ooi BC, Yang Y (2005) Tailored reversible watermarking schemes for authentication of electronic clinical atlas. IEEE Trans Inf Technol Biomed 9 (4):554–563. https://doi.org/10.1109/TITB.2005.855556
Coatrieux G, Guillou CL, Cauvin J, Roux C (2009) Reversible watermarking for knowledge digest embedding and reliability control in medical images. IEEE Trans Inf Technol Biomed 13(2):158–165. https://doi.org/10.1109/TITB.2008.2007199
Chung K, Huang Y, Chang P, Liao HM (2010) Reversible data hiding-based approach for intra-frame error concealment in h.264/AVC. IEEE Trans Circ Syst Vid Technol 20(11):1643–1647. https://doi.org/10.1109/TCSVT.2010.2077577
Wang X, Shao C, Xu X, Niu X (2007) Reversible Data-Hiding scheme for 2-D vector maps based on difference expansion. IEEE Transactions on Information Forensics and Security 2(3):311–320. https://doi.org/10.1109/TIFS.2007.902677
Luo l., Chen Z, Chen M, Zeng X, Xiong Z (2010) Reversible image watermarking using interpolation technique. IEEE Transactions on Information Forensics and Security 5(1):187–193. https://doi.org/10.1109/TIFS.2009.2035975
Malik A, Sikka G, Verma HK (2018) An AMBTC compression based data hiding scheme using pixel value adjusting strategy. Multidim System Signal Process 29:1801–1818. https://doi.org/10.1007/s11045-017-0530-8
Lin J, Weng S, Zhang T, Ou B, Chang C (2020) Two-Layer Reversible Data Hiding Based on AMBTC Image With (7, 4) Hamming Code. IEEE Access 8:21534–21548. https://doi.org/10.1109/ACCESS.2019.2962230
Tian J (2002) Wavelet-based reversible watermarking for authentication. Proceedding SPIE 4675:679–690. https://doi.org/10.1117/12.465329
Tian J (2003) Reversible data embedding using a difference expansion. IEEE Trans Circ Syst Vid Technol 13(8):890–896. https://doi.org/10.1109/TCSVT.2003.815962
Alattar AM (2004) Reversible watermark using the difference expansion of a generalized integer transform. IEEE Trans Image Process 13(8):1147–1156. https://doi.org/10.1109/TIP.2004.828418
Kamstra L, Heijmans HJAM (2005) Reversible data embedding into images using wavelet techniques and sorting. IEEE Trans Image Process 14(12):2082–2090. https://doi.org/10.1109/TIP.2005.859373
Lee S, Yoo CD, Kalker T (2007) Reversible image watermarking based on integer-to-integer wavelet transform. IEEE Transactions on Information Forensics and Security 2(3):321–330. https://doi.org/10.1109/TIFS.2007.905146
Hu Y, Lee H, Chen K, Li J (2008) Difference expansion based reversible data hiding using two embedding directions. IEEE Transactions on Multimedia 10(8):1500–1512. https://doi.org/10.1109/TMM.2008.2007341
Quershi OMA, Khoo BE (2013) Two dimensional difference expansin (2d-DE) scheme with a characteristics based threshold. Signal Process 93:154–162. https://doi.org/10.1016/j.sigpro.2012.07.012
Chen CC, Tsai YH, Yeh HC (2017) Difference expansion based reversible and visible image watermarking scheme. Multimedia Tools and Applications 76 (8497–8516):1500–1512. https://doi.org/10.1007/s11042-016-3452-9
Arham A, Nugroha HA, Adji TB (2017) Multiple layer data hiding scheme based on difference expansion of Quad. Signal Process 137:52–62. https://doi.org/10.1016/j.sigpro.2017.02.001
Thodi DM, Rodriguez JJ (2004) Prediction-error based reversible watermarking. International Conference on Image Processing, 2004 ICIP ’04 3:1549–1552. https://doi.org/10.1109/ICIP.2004.1421361
Thodi DM, Rodriguez JJ (2007) Expansion embedding techniques for reversible watermarking. IEEE Trans Image Process 16(3):721–730. https://doi.org/10.1109/TIP.2006.891046
Hu Y, Lee H, Li J (2009) DE-based reversible data hiding with improved overflow location map. IEEE Trans Circ Syst Vid Technol 19(2):250–260. https://doi.org/10.1109/TCSVT.2008.2009252
Sachnev V, Kim HJ, Nam J, Suresh S, Shi YQ (2009) Reversible watermarking algorithm using sorting and prediction. IEEE Trans Circ Syst Vid Technol 19(7):989–999. https://doi.org/10.1109/TCSVT.2009.2020257
Coltuc D (2011) Improved embedding for Prediction-Based reversible watermarking. IEEE Transactions on Information Forensics and Security 6(3):873–882. https://doi.org/10.1109/TIFS.2011.2145372
Li X, Yang B, Zeng T (2011) Efficient reversible watermarking based on adaptive prediction-error expansion and pixel selection. IEEE Trans Image Process 20(12):3524–3533. https://doi.org/10.1109/TIP.2011.2150233
Coltuc D (2012) Low distortion transform for reversible watermarking. IEEE Trans Image Process 21(1):412–417. https://doi.org/10.1109/TIP.2011.2162424
Yang S (2020) Saliency-Based Image contrast enhancement with reversible data hiding. In: IEEE international conference on acoustics, Speech and Signal Processing (ICASSP), pp 2847–2851. https://doi.org/10.1109/ICASSP40776.2020.9053103
Li X, Li J, Yang B (2013) High-fidelity reversible data hiding scheme based on pixel-value-ordering and prediction-error expansion. Signal Process 93(1):198–205. https://doi.org/10.1016/j.sigpro.2012.07.025
Peng F (2013) Improved IVO-based reversible data hiding. Digital Signal Process 25:255–265
Ou B, Li X, Zhao Y, Ni R, Shi N (2013) Pairwise Prediction-Error expansion for efficient reversible data hiding. IEEE Trans Image Process 22(12):5010–5021. https://doi.org/10.1109/TIP.2013.2281422
Ou B, Li X, Zhao Y, Ni R (2014) Reversible data hiding using invariant pixel-value-ordering and prediction-error expansion. Signal Process 29(7):760–772. https://doi.org/10.1016/j.image.2014.05.003
Kumar M, Agarwal S (2016) Reversible data hiding based on prediction error expansion using adjacent pixels. Secur Commun Netw 9(16):574–578. https://doi.org/10.1002/sec.1575
Jain NK, Kasana S (2018) High capacity reversible data hiding using modified pixel value ordering approach. J Circ Syst Comput 27(11):1850175. https://doi.org/10.1142/S021812661850175X
Zhang H, Wang C, Wang J, Xiang S (2019) A new reversible watermarking scheme using the content-adaptive block size for prediction. Signal Process 164:74–83. https://doi.org/10.1016/j.sigpro.2019.05.035
Abbasi R, Qureshi NMF., Hassan H (2019) Generalized PVO-based dynamic block reversible data hiding for secure transmission using firefly algorithm. Transaction on Emerging Telecommunications Technologies. https://doi.org/10.1002/ett.3680
Uyyala R, Pal R (2020) Reversible data hiding using improved gradient based prediction and adaptive histogram bin shifting. In: 7th International Conference on Signal Processing and Integrated Networks (SPIN), pp 720–726. https://doi.org/10.1109/SPIN48934.2020.9071246
Wu H (2020) Patch-Level Selection and Breadth-First prediction strategy for reversible data hiding. In: 2020 IEEE international conference on acoustics, Speech and Signal Processing (ICASSP). https://doi.org/10.1109/ICASSP40776.2020.9054386
Kumar R, Jung KH (2020) Robust reversible data hiding scheme based on two-layer embedding strategy. Inf Sci 512:96–107. https://doi.org/10.1016/j.ins.2019.09.062
Li N, Huang F (2020) Reversible data hiding for JPEG images based on pairwise nonzero AC coefficient expansion. Signal Process 107476:171. https://doi.org/10.1016/j.sigpro.2020.107476
Ni N, Shi YQ, Ansari N, Su W (2006) Reversible data hiding. IEEE Trans Circ Syst Vid Technol 16(3):354–362. https://doi.org/10.1109/TCSVT.2006.869964
Vleeschouwer CD, Delaigle JE, Macq B (2001) Circular interpretation of histogram for reversible watermarking. 2001 IEEE Fourth Workshop on Multimedia Signal Processing (Cat. No.01TH8564), pp 345–350. https://doi.org/10.1109/MMSP.2001.962758
Fallahpour M, Sedaaghi MH (2007) High capacity lossless data hiding based on histogram modification. IEICE Electronics Express 4(7):205–210. https://doi.org/10.1587/elex.4.205
Lee S, Suh Y, Ho Y (2006) Reversible image authentication based on watermarking. In: 2006 IEEE International Conference on Multimedia and Expo, pp 1321–1324. https://doi.org/10.1109/ICME.2006.262782
Lin CC, Tai WL, Chang CC (2008) Multilevel reversible data hiding based on histogram modification of difference images. Pattern Recogn 41(12):3582–3591. https://doi.org/10.1016/j.patcog.2008.05.015
Tai W, Yeh C, Chang C (2009) Reversible data hiding based on histogram modification of pixel differences. IEEE Trans Circ Syst Vid Technol 19(6):906–910. https://doi.org/10.1109/TCSVT.2009.2017409
Gao X, An L, Yuan Y, Tao D, Li X (2011) Lossless data embedding using generalized statistical quantity histogram. IEEE Trans Circ Syst Vid Technol 21(8):1061–1070. https://doi.org/10.1109/TCSVT.2011.2130410
Li X, Li B, Yang B, Zeng T (2013) General framework to Histogram-Shifting-Based reversible data hiding. IEEE Trans Image Process 22(6):2181–2191. https://doi.org/10.1109/TIP.2013.2246179
Fujiyoshi M, Sato S, Jin HL, Kiya H (2007) A location-map free reversible data hiding method using block-based single parameter. 2007 IEEE International Conference on Image Processing 3:257–260. https://doi.org/10.1109/ICIP.2007.4379295
Fujiyoshi M, Tsuneyoshi T, Kiya H (2010) A parameter memorization-free lossless data hiding method with flexible payload size. IEICE Electronics Express 7(23):1702–1708. https://doi.org/10.1587/elex.7.1702
Li X, Zhang W, Gui X, Yang B (2013) A novel reversible data hiding scheme based on Two-Dimensional Difference-Histogram modification. IEEE Transactions on Information Forensics and Security 8(7):1091–1100. https://doi.org/10.1109/TIFS.2013.2261062
Li X, Zhang W, Gui X, Yang B (2015) Efficient reversible data hiding based on multiple histograms modification. IEEE Transactions on Information Forensics and Security 10(9):2016–2027. https://doi.org/10.1109/TIFS.2015.2444354
Garg P, Kasana SS, Kasana G (2017) Block-based reversible data hiding using histogram shifting and modulus operator for digital images. J Circ Syst Comput 26(6):1750103–1750120. https://doi.org/10.1142/S0218126617501031
Qi W, Li X, Zhang T, Guo Z (2019) Optimal reversible data hiding scheme based on multiple histograms modification. IEEE Trans Circ Syst Vid Technol 30(8):2300–2312. https://doi.org/10.1109/TCSVT.2019.2942489
Ou B, Zhao Y (2019) High capacity reversible data hiding based on multiple histograms modification. IEEE Trans Circ Syst Vid Technol 30(8):2329–2342. https://doi.org/10.1109/TCSVT.2019.2921812
He X, Zhang W, Zhang H, Ma L, Li Y (2019) Reversible data hiding for high dynamic range images using edge information. Multimedia Tools Applied 78:29137–29160. https://doi.org/10.1007/s11042-018-6589-x
Jia Y, Yina Z, Zhang X, Luo Y (2019) Reversible data hiding based on reducing invalid shifting of pixels in histogram shiftin. Signal Process 163:238–246. https://doi.org/10.1016/j.sigpro.2019.05.020
Gao X, Pan Z, Gao E, Fan G (2020) Reversible data hiding for high dynamic range images using two-dimensional prediction-error histogram of the second time prediction. Signal Process 173:107579. https://doi.org/10.1016/j.sigpro.2020.107579
Shaji C, Sam S (2019) A new data encoding based on maximum to minimum histogram in reversible data hiding. The Imaging Journal 67(4):202–214. https://doi.org/10.1080/13682199.2019.1592892
Wang J, Chen X, Ni J, Mao N, Shi Y (2019) Multiple histograms based reversible data hiding: framework and realization. IEEE Trans Circ Syst Vid Technol 30(8):2313–2328. https://doi.org/10.1109/TCSVT.2019.2915584
Manikandan VM, Renjith P (2020) An efficient overflow handling technique for histogram shifting based reversible data hiding. In: 2020 International Conference on Innovative Trends in Information Technology (ICITIIT), pp 1–6. https://doi.org/10.1109/ICITIIT49094.2020.9071553
He J, Chen J, Tang S (2020) Reversible data hiding in JPEG images based on negative influence models. IEEE Transactions on Information Forensics and Security 15:2121–2133. https://doi.org/10.1109/TIFS.2019.2958758
Wang W, Wang W (2020) HS-Based reversible data hiding scheme using median prediction error. Multimedia Tools and Applications 79:18143–18165. https://doi.org/10.1007/s11042-020-08682-3
Jung KH, Yoo KY (2009) Data hiding method using image interpolation. Computer Satandards and Interfaces 31(2):465–470. https://doi.org/10.1016/j.csi.2008.06.001
Yalman Y, Akar F, Erturk I (2010) An image interpolation based reversible data hiding method using r-weighted coding. In: 2010 13th IEEE International Conference on Computational Science and Engineering, pp 346–350. https://doi.org/10.1109/CSE.2010.52
Lee CF, Huang YL (2012) An efficient image interpolation increasing payload in reversible data hiding. Expert Syst Appl 39(8):6712–6719. https://doi.org/10.1016/j.eswa.2011.12.019
Tsai YY, Chen JT, Kuo YC, Chan CS (2014) A generalized image interpolation -based reversible data hiding scheme with high embedding capacity and image quality. KSSI Trans Internet Inform Syst 8 (9):3286–3301. https://doi.org/10-3837/tiis.2014.09.019
Chang YT, Huang CT, Lee CF, Wang SJ (2013) Image interpolating based data hiding in conjunction with pixel-shifting of histogram. J Supercomput 66:1093–1110. https://doi.org/10.1007/s11227-013-1016-6
Loua DC, Choub CL, Weia HY, Huang HF (2013) Active steganalysis for interpolation-error based reversible data hiding. Pattern Recogn Lett 34 (9):1032–1036. https://doi.org/10.1016/j.patrec.2013.01.023
Wang XT, Chang CC, Nguyen TS (2013) Reversible data hiding for high quality images exploiting interpolation and direction order mechnism. Digital Signal Process 23 (2):569–577. https://doi.org/10.1016/j.dsp.2012.06.015
Hu J, Li T (2015) Reversible steganography using extended image interpolation. Comput Electr Eng 46:447–455. https://doi.org/10.1016/j.compeleceng.2015.04.014
Wahed MA, Nyeem H (2017) Efficient LSB substitution for interpolation based reversible data hiding scheme. In: 2017 20th International Conference of Computer and Information Technology (ICCIT), pp 1–6. https://doi.org/10.1109/ICCITECHN.2017.8281771
Malik A, Sikka G, Verma HK (2017) An image interpolation based reversible data hiding scheme using pixel value adjusting feature. Multimedia Tools Applied 76:13025–13046. https://doi.org/10.1007/s11042-016-3707-5
Zhang X, Sun Z, Tang Z, Yu C, Wang X (2017) High capacity data hiding based on interpolated image. Multimedia Tools Applications 76:9195–9218. https://doi.org/10.1007/s11042-016-3521-0
Shaik A (2018) High capacity data hiding using 2D parabolic interpolation. Multimedia Tools and Applications 78:9717–9735. https://doi.org/10.1007/s11042-018-6544-x
Khosravi MR, Yazdi M (2018) A lossless data hiding scheme for medical images using a hybrid solution based on IBRW error histogram computation and quartered interpolation with greedy weights. Neural Computing and applications 30:2017–2028. https://doi.org/10.1007/s00521-018-3489-y
Jana M, Jana B (2020) An improved data hiding scheme through image interpolation. Comput Intell Pattern Recognition 999:157–169. https://doi.org/10.1007/978-981-13-9042-5_14
Malik A, Sikka G, Verma HK (2020) A reversible data hiding scheme for interpolated images based on pixel intensity range. Multimedia Tools Applications 79:18005–18031. https://doi.org/10.1007/s11042-020-08691-2
Puech W, Chaumont M, Strauss O (2008) A reversible data hiding method for encrypted images. SPIE 6819. https://doi.org/10.1117/12.766754
Zhang X (2011) Reversible data hiding in encrypted image. IEEE Signal Process Lett 18 (4):255–258. https://doi.org/10.1109/LSP.2011.2114651
Hong W, Chen T, Wu H (2012) An improved reversible data hiding in encrypted images using side match. IEEE Signal Process Lett 19(4):199–202. https://doi.org/10.1109/LSP.2012.2187334
Yu J, Zhu G, Li X, Yang J (2016) An improved algorithm for reversible data hiding in encrypted image. The International Workshop on Digital Forensics and Watermarking 2012. LNCS 7809(3):441–452. https://doi.org/10.1007/978-3-642-40099-5_32
Liao X, Shu C (2015) Reversible data hiding in encrypted images based on absolute mean difference of multiple neighboring pixels. J Vis Commun Image Represent 28:21–27. https://doi.org/10.1016/j.jvcir.2014.12.007
Qian Z, Zhang X (2016) Reversible data hiding in encrypted images with distributed source encoding. IEEE Trans Circ Syst Vid Technol 26(4):636–646. https://doi.org/10.1109/TCSVT.2015.2418611
Zhang R, Lu C, Liu J (2019) A high capacity reversible data hiding scheme for encrypted covers based on histogram shifting. J Inform Secur Appl 47:199–207. https://doi.org/10.1016/j.jisa.2019.05.005
Abhinav A, Manikandan VM, AAB (2020) An improved reversible data hiding on encrypted images by selective pixel flipping technique. 2020 5th International Conference on Devices, Circuits and Systems (ICDCS), pp 294–298. https://doi.org/10.1109/ICDCS48716.2020.243602
Kumaresan G, Gopalan NP (2020) Reversible data hiding in encrypted images using public cloud and cellular Automata. J Appl Sec Res 15:427–444. https://doi.org/10.1080/19361610.2019.1656472
Zhang X (2012) Separable reversible data hiding in encrypted image. IEEE Transactions on Information Forensics and Security 7(2):826–832. https://doi.org/10.1109/TIFS.2011.2176120
Xiao D, Chen S (2014) Separable data hiding in encrypted image based on compressive sensing. Electron Lett 50(8):598–600
Zhang X, Qian Z, Feng G, Ren Y (2014) Efficient reversible data hiding in encrypted images. J Visual Commun Image Represent 25(2):322–328. https://doi.org/10.1016/j.jvcir.2013.11.001
Zhang X, Qin C, Sun G (2012) Reversible data hiding in encrypted images using pseudorandom sequence modulation. IWDW 2012: The International Workshop on Digital Forensics and Watermarking 2012. LNCS 25:358–367. https://doi.org/10.1007/978-3-642-40099-5_30
Chen YC, Shiu CW, Horng G (2014) Encrypted Signal-based reversible data hiding with public key cryptosystem. J Vis Commun Image Represent 25(5):1164–1170. https://doi.org/10.1016/j.jvcir.2014.04.003
Wu X, Sun W (2014) High-capacity reversible data hiding in encrypted images by prediction error. Signal Processsing 104:387–400. https://doi.org/10.1016/j.sigpro.2014.04.032
Zheng S, Li D, Hu D, Ye D, Wang L, Wang J (2016) Lossless data hiding algorithm for encrypted images with high capacity. Multimedia Tools and Applications 75:13765–13778
Yin Z, Abel A, Tang J, Zhang X, Luo B (2017) Reversible data hiding in encrypted images based on multi-level encryption and block histogram modification. Multimedia Tools and Applications 76 (3):3899–3920. https://doi.org/10.1007/s11042-016-4049-z
Qian Z, Zhang X, Ren Y, Feng G (2017) Block cipher based separable reversible data hiding in encrypted image. Multimedia Tools and Applications 75(3):13749–13763. https://doi.org/10.1007/s11042-015-2760-9
Yi S, Zhou Y, Hua Z (2018) Reversible data hiding in encrypted images using adaptive block-level prediction-error expansion. Signal Process 64:78–88. https://doi.org/10.1016/j.image.2018.03.001
Li Q, Yan B, Li H, Chen N (2018) Separable reversible data hiding in encrypted images with improved security and capacity. Multimedia Tools and Applications 77 (4):30749–30768. https://doi.org/10.1007/s11042-018-6187-y
Zhang R, Lu C, Liu J (2019) A high capacity reversible data hiding scheme for encrypted covers based on histogram shifting. Inform Secur 47:199–207. https://doi.org/10.1016/j.jisa.2019.05.005
Tang Z, Xu S, Yao H, Qin C, Zhang X (2019) Reversible data hiding with differential compression in encrypted image. Multimedia Tools and Applications 78:9691–9715. https://doi.org/10.1007/s11042-018-6567-3
Huang D, Wang J (2019) High-capacity reversible data hiding in encrypted image based on specific encryption process. Signal Processing: Image Communication 80:Article ID 115632. https://doi.org/10.1016/j.image.2019.115632
Xiang S, Luo X (2018) Reversible data hiding in homomorphic encrypted domain by mirroring ciphertext group. IEEE Trans Circ Syst Vid Technol 28(11):3099–3110. https://doi.org/10.1109/TCSVT.2017.2742023
Zhou N, Zhang M, Wang H, Ke Y, Di F (2020) Separable reversible data hiding scheme in homomorphic encrypted domain based on NTRU. IEEE Access 8:81412–81424. https://doi.org/10.1109/ACCESS.2020.2990903
Khan A, Siddiqa A, Munib S, Malik SA (2014) A recent survey of reversible watermarking techniques. Inform Sci 279:251–272. https://doi.org/10.1007/s11042-017-5066-2
Shi Y, Li X, Zhang X, Wu H, Ma B (2016) Reversible data hiding: Advances in the past two decades. IEEE Access 4:3210–3237. https://doi.org/10.1109/ACCESS.2016.2573308
Luo L, Chen Z, Chen M, Zeng X, Xiong Z (2010) Reversible image watermarking using interpolation technique. IEEE Transactions on Information Forensics and Security 5(1):187–193. https://doi.org/10.1109/TIFS.2009.2035975
Jung KH (2017) A survey of interpolation-based reversible data hiding methods. Multimedia Tools and Applications 77(7):7795–7810. https://doi.org/10.1007/s11042-017-5066-2
Sen S, Mukherjee A, Mondal J, Saroliya A (2020) A contemplator on reversible data hiding in encrypted domain. In: 2020 international conference on emerging trends in communication, Control and Computing (ICONC3) pp 1–4. https://doi.org/10.1109/ICONC345789.2020.9117341
Zhang X, Long J, Wang Z, Cheng H (2016) Lossless and reversible data hiding in encrypted images with Public-Key cryptography. IEEE Trans Circ Syst Vid Technol 26(9):1622–1631. https://doi.org/10.1109/TCSVT.2015.2433194
Ma K, Zhang W, Zhao X, Yu N, Li F (2013) Reversible data hiding in encrypted images by reserving room before encryption. IEEE Transactions on Information Forensics and Security 8 (3):553–562. https://doi.org/10.1109/TIFS.2013.2248725
Mathew T, Wilscy M (2014) Reversible data hiding in encrypted images by active block exchange and room reservation. In: 2014 International Conference on Contemporary Computing and Informatics (IC3I), pp 839–844. https://doi.org/10.1109/IC3I.2014.7019628
Cao X, Du L, Wei X, Meng D, Guo X (2016) High capacity reversible data hiding in encrypted images by Patch-Level sparse representation. IEEE Trans Cybern 46(5):1132–1143. https://doi.org/10.1109/TCYB.2015.2423678
Qian Z, Zhang X, Feng G (2016) Reversible data hiding in encrypted images based on progressive recovery. IEEE Signal Process Lett 23(11):1672–1676. https://doi.org/10.1109/LSP.2016.2585580
Zhang W, MA K, Yu N (2013) Reversibility improved data hiding in encrypted images. Signal Process 94:118–127. https://doi.org/10.1016/j.sigpro.2013.06.023
Zhou J, Sun W, Dong L, Liu X, Au OC, Tang Y (2016) Secure reversible image data hiding over encrypted domain via key modulation. IEEE Trans Circ Syst Vid Technol 26(3):441–452. https://doi.org/10.1109/TCSVT.2015.2416591
Yi S, Zhou Y (2019) Separable and reversible data hiding in encrypted images using parametric binary tree labeling. IEEE Transactions on Multimedia 21 (1):51–64. https://doi.org/10.1109/TMM.2018.2844679
Wu Y, Xiang Y, Guo Y, Tang J, Yin Z (2019) An improved reversible data hiding in encrypted images using parametric binary tree labeling. IEEE Transactions on Multimedia 22(8):1929–1938. https://doi.org/10.1109/TMM.2019.2952979
Mohammadi A, Nakhkash M, Akhaee MA (2020) A High-Capacity reversible data hiding in encrypted images employing local difference predictor. IEEE Trans Circ Syst Vid Technol 30(8):2366–2376. https://doi.org/10.1109/TCSVT.2020.2990952
Malik A, Wang HX, Chen Y, Khan AN (2020) A reversible data hiding in encrypted image based on prediction-error estimation and location map. Multimedia Tools and Applications 79:11591–11614. https://doi.org/10.1007/s11042-019-08460-w
Puteaux P, Puech W (2018) EPE-based huge-capacity reversible data hiding in encrypted images. 2018 IEEE International Workshop on Information Forensics and Security (WIFS) pp 1–7. https://doi.org/10.1109/WIFS.2018.8630788
Puteaux P, Puech W (2020) A recursive reversible data hiding in encrypted images method with a very high payload. IEEE Transactions on Multimedia 23:636–650. https://doi.org/10.1109/TMM.2020.2985537
Yin Z, Xiang Y, Zhang X (2020) Reversible data hiding in encrypted images based on multi-MSB prediction and huffman coding. IEEE Transactions on Multimedia 22(4):874–884. https://doi.org/10.1109/TMM.2019.2936314
Yu M, Liu Y, Sun H, Yao H, Qiao T (2020) Adaptive and separable multiary reversible data hiding in encryption domain. EURASIP J Image Vid Process 16:2020. https://doi.org/10.1186/s13640-020-00502-w
Wu Y, Ma W, Peng Y, Zhang R, Yin Z (2020) Reversible data hiding in encrypted images based on bit plane compression of prediction error. Scientific World Jurnal 2:1–18. https://doi.org/10.1145/nnnnnnn.nnnnnnn
Yin Z, Luo B (2020) Hong w Separable and error-free reversible data hiding in encrypted image with high payload. IEEE Transactions on Information Forensics and Security 2014:Article ID 604876. https://doi.org/10.1155/2014/604876
Huang F, Huang J, Shi Y (2016) New framework for reversible data hiding in encrypted domain. EEE Transactions on Information Forensics and Security 11(12):2777–2789. https://doi.org/10.1109/TIFS.2016.2598528
Di F, Huang f., Zhang m., Liu J, Yang X (2018) Reversible data hiding in encrypted images with high capacity by bit-plane operations and adaptive embedding. Multimedia Tools and Applications 77:20917–20935. https://doi.org/10.1007/s11042-017-5498-8
Qian Z, Xu H, Luo X, Zhang X (2019) New framework of reversible data hiding in encrypted JPEG bitstreams. IEEE Trans Circ Syst Vid Technol 29(2):351–362. https://doi.org/10.1109/TCSVT.2018.2797897
Peng F, Li X, Yang B (2012) Adaptive reversible data hiding scheme based on integer transform. Signal Process 92(1):54–62. https://doi.org/10.1016/j.sigpro.2011.06.006
Qiu Y, Qian Z, Yu L (2016) Adaptive reversible data hiding by extending the generalized integer transformation. IEEE Signal Process Lett 23(1):130–134. https://doi.org/10.1109/LSP.2015.2504464
Chen K, Chang CC (2019) High-capacity reversible data hiding in encrypted images based on extended run-length coding and block-based MSB plane rearrangement. J Visual Commun Image Represent 58:334–344. https://doi.org/10.1016/j.jvcir.2018.12.023
Puteaux P, Puech W (2018) An efficient MSB Prediction-Based method for High-Capacity reversible data hiding in encrypted images. IEEE Transactions on Information Forensics and Security 13(7):1670–1681. https://doi.org/10.1109/TIFS.2018.2799381
Dragoi IC, Coltuc D (2020) On the security of reversible data hiding in encrypted images by MSB prediction. IEEE Transactions on Information Forensics and Security 16:187–189. https://doi.org/10.1109/TIFS.2020.3006382
Puyang Y, Yin Z, Qian Z (2018) Reversible data hiding in encrypted images with Two-MSB prediction. 2018 IEEE International Workshop on Information Forensics and Security (WIFS. https://doi.org/10.1109/WIFS.2018.8630785
Chen F, Yuan Y, He H, Tian M, Tai H (2020) Multi-MSB compression based reversible data hiding scheme in encrypted images. IEEE Trans Circ Syst Vid Technol 31 (3):905–916. https://doi.org/10.1109/TCSVT.2020.2992817
Li M, Li Y (2017) Histogram shifting in encrypted images with public key cryptosystem for reversible data hiding. Signal Process 130:190–196. https://doi.org/10.1016/j.sigpro.2016.07.002
Jiang C, Pang Y (2020) Encrypted images-based reversible data hiding in Paillier cryptosystem. Multimedia Tools and Applications 79:693–711. https://doi.org/10.1007/s11042-019-07874-w
Wang Y, Cai Z, He W (2020) High capacity reversible data hiding in encrypted image based on intra-block lossless compression. IEEE Transactions on Multimedia 23:1466–1473. https://doi.org/10.1109/TMM.2020.2999187
Liu J, Zhao K, Zhang R (2020) A fully reversible data hiding scheme in encrypted images based on homomorphic encryption and pixel prediction. Circ Syst Signal Process 39:3532–3552. https://doi.org/10.1007/s00034-019-01321-9
Ke Y, Zhang M, Liu J, Su T, Yang X (2019) Fully homomorphic encryption encapsulated difference expansion for reversible data hiding in encrypted domain. IEEE Trans Circ Syst Vid Technol 30(8):2353–2365. https://doi.org/10.1109/TCSVT.2019.2963393
Daubechies I, Sweldens W (1998) Factoring wavelet transforms into lifting steps. J Fourier Anal Appl 4:247–269
Witten IH, Radford M, Cleary JG (1987) Arithmetic coding for data compression. Communications of the ACM. https://doi.org/10.1145/214762.214771
Stallings W (2003) Cryptography and Network security: Principles and Practice. 3rd ed. Upper Saddle River, NJ USA: Prentice-Hall
Signal image process Inst. Univ. Southern California, Los Angeles image Database [Online]. Available:http://sipi.usc.edu/database
Bas P, Filler T, Pevny T (2011) Break Our Steganographic System”: The Ins and Outs of Organizing BOSS. IH 2011: Information Hiding, LNCS 6958:59-70. https://doi.org/10.1007/978-3-642-24178-9_5
Franzen R (2014) Kodak Lossless True Color Image Suite. http://www.r0k.us/graphics/kodak 28(3)
Garcia JA, Sanchez RR (2002) CVG-UGR Image Data Base. http://decsai.ugr.es/cvg/dbimagenes/index.php
Schaefer G, Stich M (2004) UCID-An uncompressed color image database. In: Proc SPIE Storage and Retrieval Methods and Applications for Multimedia, pp 472–480
Brodatz P., Bas P., Furon T. (1966) Brodatz database. Textures: A Photographic Album for Artists and Designers. https://en.wikipedia.org/wiki
Brodatz P., Bas P., Furon T. (2008) Bows-2: Break over watermark system Second Eddition. https://doi.org/10.1117/12.704969
Tao D (2009) The COREL Database for Content based Image Retrieval. https://sites.google.com/site/dctresearch/Home/content-based-image-retrieval
Jegou H, Douze M, Schmid C (2008) Hamming Embedding and Weak geometry consistency for large scale image search. In: Proceedings of the 10th European conference on Computer vision
Li M, Xiao D, Zhang Y, Nan H (2015) Reversible data hiding in encrypted images using cross division and additive homomorphism. Signal Process Image Commun 39:234–248. https://doi.org/10.1016/j.image.2015.10.001
Zhang W, Wang H, Hou D, Yu N (2016) Reversible data hiding in encrypted images by reversible image transformation. IEEE Transactions on Multimedia 18(8):1469–1479. https://doi.org/10.1109/TMM.2016.2569497
Liu ZL, Pun CM (2018) Reversible data hiding in encrypted images by redundant space transfer. Inf Sci 433:188–203. https://doi.org/10.1016/j.ins.2017.12.044
Ge H, Chen Y, Qian Z, Wang J (2019) A high capacity Multi-Level approach for reversible data hiding in encrypted images. IEEE Trans Circ Syst Vid Technol 29(8):2285–2295. https://doi.org/10.1109/TCSVT.2018.2863029
Fu Y, Kong P, Yao H, Tang Z, Qin C (2019) Effective reversible data hiding in encrypted image with adaptive encoding strategy. Inf Sci 494:21–36. https://doi.org/10.1016/j.ins.2019.04.043
Liu ZL, Pun CM (2020) Reversible data hiding in encrypted images using chunk encryption and redundancy matrix representation. IEEE Transactions on Dependable and Secure Computing, pp 1–1. https://doi.org/10.1109/TDSC.2020.3011838
Liu ZL, Pun CM (2019) Reversible image reconstruction for reversible data hiding in encrypted images. Signal Process 161:50–62
Qin C, Qian X, Hong W, Zhang X (2019) An efficient coding scheme for reversible data hiding in encrypted image with redundancy transfer. Inf Sci 487:176–192. https://doi.org/10.1016/j.ins.2019.03.008
Lee LY, Tsai HW (2014) A new secure image transmission technique via Secret-Fragment-Visible mosaic images by nearly reversible color transformations. IEEE Trans Circ Syst Vid Technol 24(4):695–703. https://doi.org/10.1109/TCSVT.2013.2283431
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Kumar, S., Gupta, A. & Walia, G.S. Reversible data hiding: A contemporary survey of state-of-the-art, opportunities and challenges. Appl Intell 52, 7373–7406 (2022). https://doi.org/10.1007/s10489-021-02789-2
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10489-021-02789-2




